The modern cybersecurity landscape is a relentless battlefield. Security operations teams face a constant barrage of sophisticated threats, often hidden within mountains of network data. Manual threat hunting, sifting through countless logs and alerts, is no longer a sustainable strategy. The sheer speed and complexity of attacks demand a more proactive and automated approach. This is where the powerful synergy of network automation and the intelligence of Artificial Intelligence (AI) comes into play, with optimized NetFlow acting as the crucial fuel.
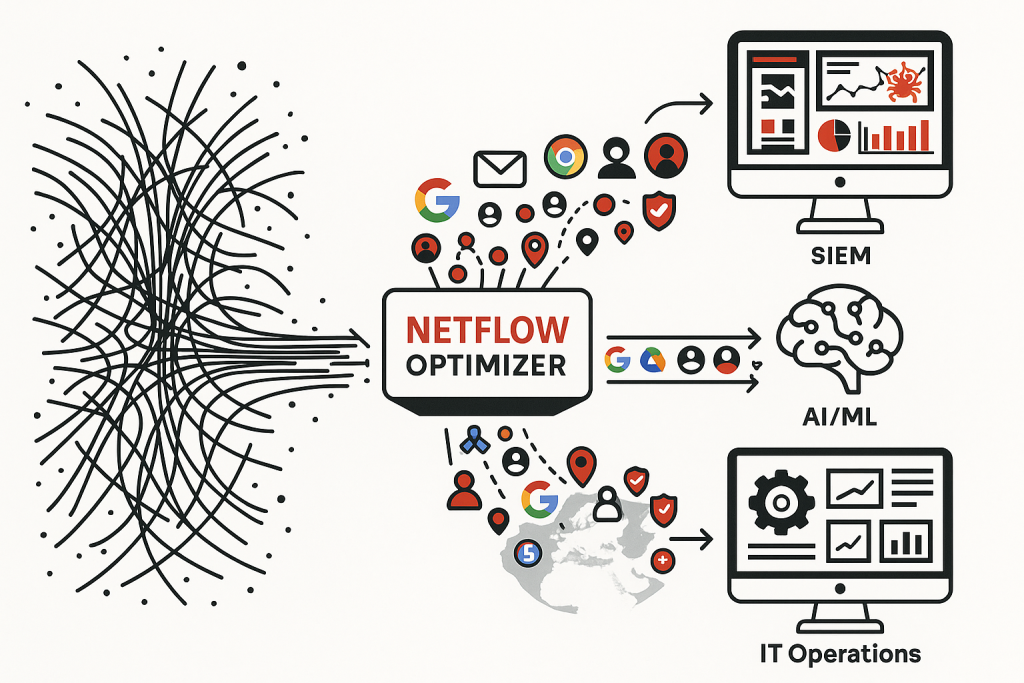
Imagine trying to detect a single malicious actor moving through a bustling city by only looking at grainy, low-resolution satellite images. That’s akin to attempting AI-driven threat hunting with raw, unoptimized NetFlow data. While NetFlow offers a wealth of information about network traffic, its notorious volume can quickly become overwhelming. Security teams are often drowning in flow records, making it nearly impossible to identify subtle anomalies that could indicate a breach. Without addressing this data deluge, even the most advanced AI algorithms will struggle to discern genuine threats from the noise.
The Bottleneck of Big Data: Why NetFlow Volume Reduction Matters for Automation
The first critical step in leveraging NetFlow for automated threat hunting is tackling its inherent scalability challenge. The sheer number of flow records generated by even moderately sized networks can cripple analysis tools and slow down automation workflows. This is where intelligent NetFlow volume reduction techniques are essential. By employing methods like deduplication (removing redundant data), aggregation (summarizing similar flows), and NetFlow stitching (reconstructing complete conversations), we can significantly decrease the data footprint without sacrificing crucial security insights. This optimized data is not only easier to store and process but also dramatically improves the efficiency of downstream AI/ML models used for automated threat hunting.
Empowering AI with Context: The Necessity of NetFlow Enrichment
Reducing the volume is only half the battle. To truly unlock the potential of AI in automated threat hunting, the data needs to be rich and meaningful. Raw NetFlow data, with its basic IP addresses and port numbers, offers a limited perspective. These “naked IP addresses,” without context, provide little actionable intelligence for sophisticated AI algorithms designed to identify subtle patterns of malicious activity.
NetFlow enrichment is the process of adding vital contextual layers to these raw records. By correlating NetFlow data with information such as:
- Application Identification: Understanding which applications are generating the traffic.
- Geolocation: Identifying the geographical origin and destination of connections.
- User Identification: Linking network activity to specific users within the organization.
- Threat Intelligence Feeds: Flagging traffic associated with known malicious entities.
- Virtual Machine (VM) Names: Providing visibility within virtualized environments.
we transform basic flow records into high-fidelity security intelligence. This enriched data provides the necessary features and context for AI/ML models to learn normal network behavior accurately and detect even the most subtle deviations indicative of an attack. Trying to automate threat hunting with un-enriched NetFlow is like trying to have an intelligent conversation with someone who only speaks in numbers – the meaning is simply lost.
Fueling Automated Responses: From Detection to Action
The combination of optimized volume and enriched context makes NetFlow data an ideal fuel for AI-driven security operations. AI/ML algorithms can be trained on this high-quality data to automatically:
- Identify anomalous network behavior that deviates from established baselines.
- Detect patterns indicative of known attack techniques, such as lateral movement or command-and-control communication.
- Prioritize alerts based on the severity and context of the identified anomalies, reducing alert fatigue for security teams.
- Trigger automated responses to contain and mitigate threats in real-time, such as isolating infected hosts or blocking malicious IP addresses.
The NetFlow Optimizer Advantage: Your Engine for AI-Driven Security Automation
Our NetFlow Optimizer is specifically designed to address the challenges of leveraging NetFlow for advanced security automation. We provide a comprehensive solution that not only intelligently reduces the volume of your raw NetFlow data but also enriches it with the critical context needed to power your AI/ML-driven threat hunting initiatives.
By providing high-quality, reduced, and enriched NetFlow data, our NetFlow Optimizer directly enables and enhances your security automation capabilities, allowing you to:
- Feed your AI/ML models with the precise data they need for accurate and efficient threat detection.
- Improve the speed and accuracy of automated threat hunting workflows.
- Reduce the strain on your security infrastructure by processing and optimizing data before it reaches your analysis tools.
- Maximize the value of your existing security investments by providing them with a richer and more actionable data source.
Don’t let the sheer volume and lack of context in your raw NetFlow data hinder your journey towards proactive and automated security.
Ready to empower your security operations with AI-driven threat hunting? Discover how our NetFlow Optimizer can provide the high-quality, reduced, and enriched data your AI needs to stay ahead of evolving threats. Visit our website today to explore our solution and request a personalized demo.
