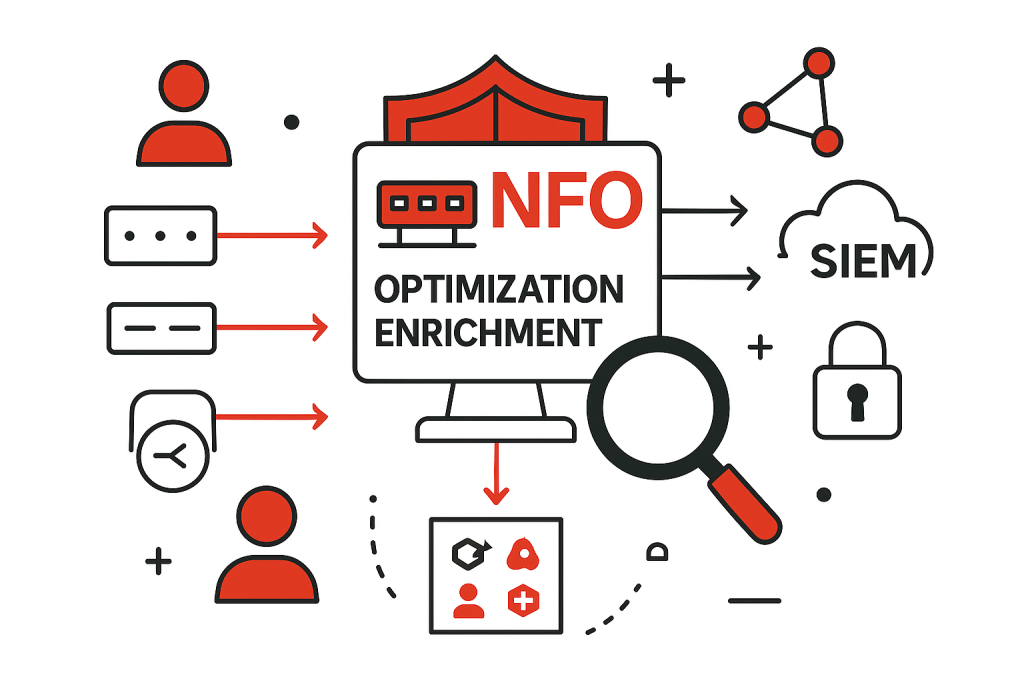
Maximizing Your Security Stack: Integrating NetFlow for Unified Visibility and AI Correlation
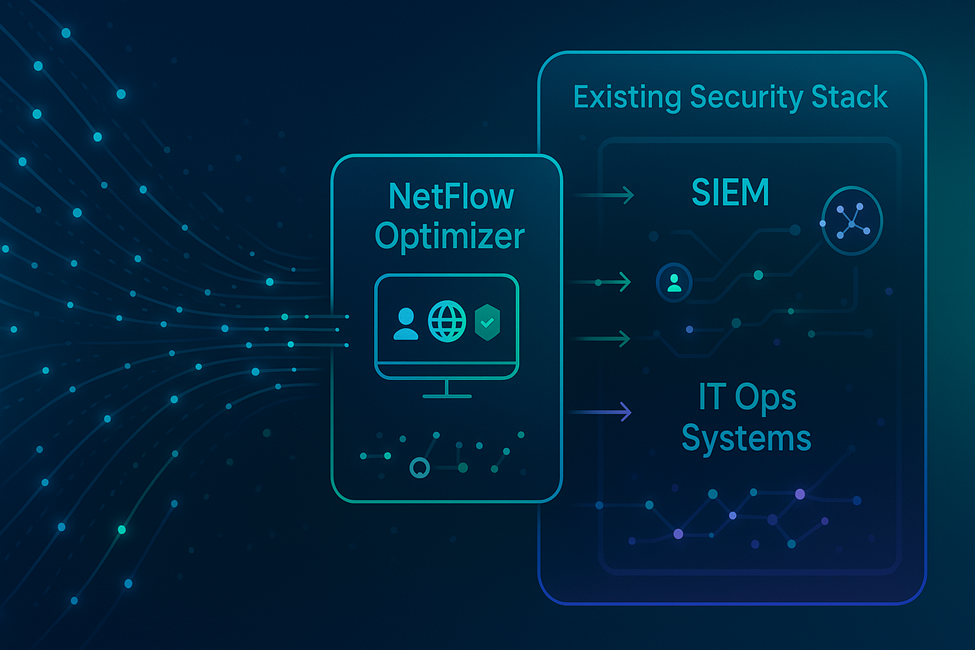
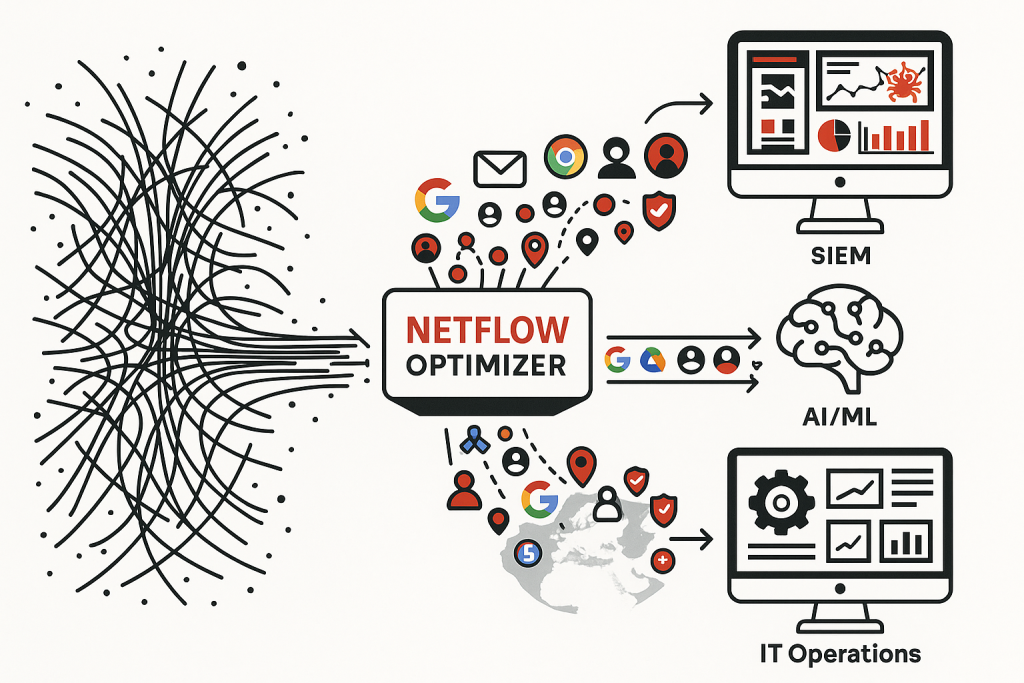
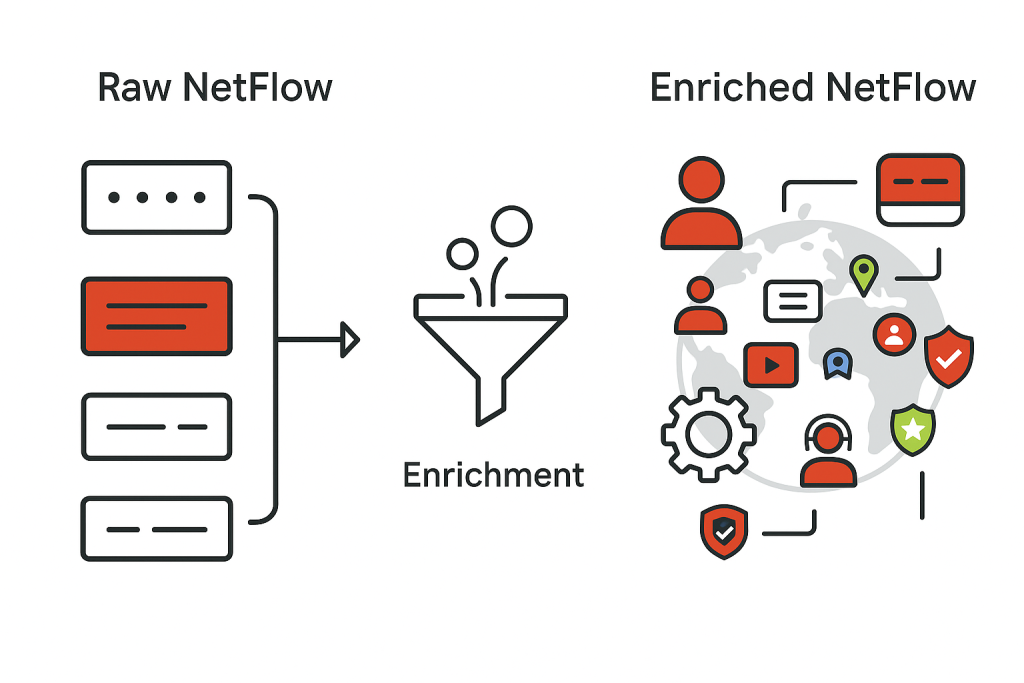
In today’s complex threat landscape, security teams constantly strive for a more comprehensive understanding of their network. While significant investments have been made in SIEM (Security Information and Event Management) and IT Operations systems, a crucial piece of the puzzle often remains underutilized: NetFlow data. NetFlow, and its brethren like IPFIX and sFlow, provides invaluable