In the modern enterprise, APIs are the connective tissue of digital business. But while security teams are busy hardening their known, documented gateways, a silent threat is growing in the background: Shadow APIs.
Shadow APIs are undocumented, unmanaged, or “zombie” endpoints—often created for testing, legacy support, or by third-party integrations—that exist outside the view of your Web Application Firewall (WAF) or API Gateway. Because they aren’t “officially” recognized, they don’t receive security patches, rate limiting, or authentication updates, making them a primary target for data exfiltration.
The Problem: You Can’t Secure What You Can’t See
Traditional API security tools often rely on a “positive security model,” meaning they protect the APIs you explicitly tell them to monitor. If an endpoint isn’t in your documentation, it isn’t being defended. Attackers use automated tools to scan your network for these forgotten paths, searching for:
- Legacy Endpoints: Old versions of APIs (e.g., /v1/users) that were never shut down but still maintain database access.
- Developer Backdoors: Temporary APIs created for troubleshooting or “quick fixes” that were accidentally left active in production.
- Shadow IT Services: Applications spun up by individual departments that create their own API connections without informing the central IT or security teams.
The Solution: Discovery Enabled by Enriched Telemetry
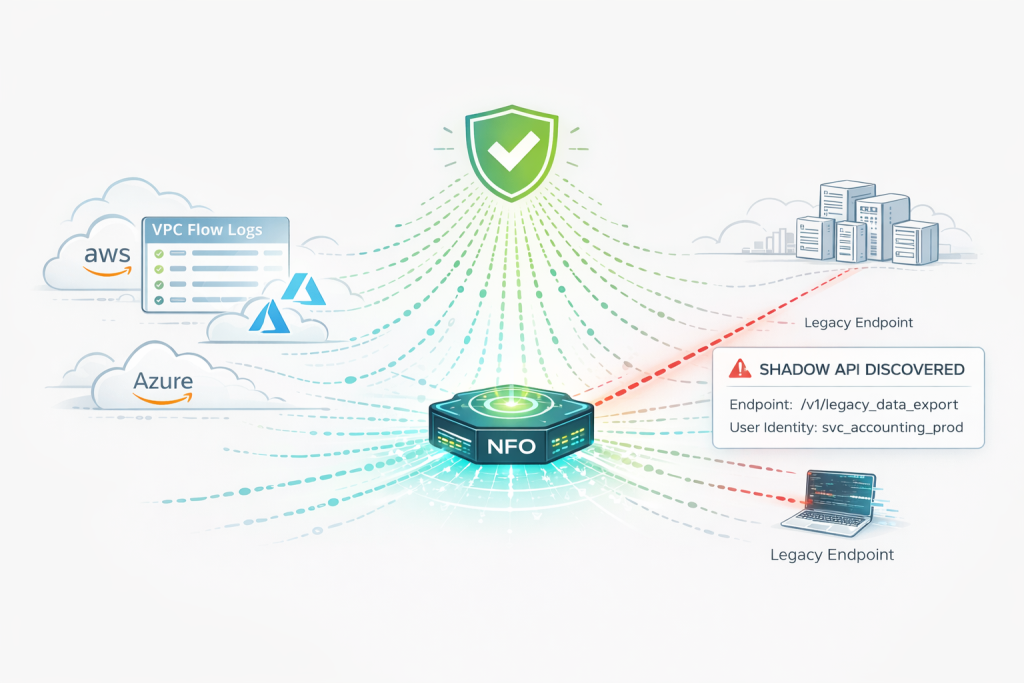
To find Shadow APIs, you have to look at actual network behavior, not just documentation. While your API Gateway only sees the traffic you’ve routed through it, NetFlow Optimizer (NFO) sees everything else.
NFO serves as the critical bridge, collecting raw flow data from across your hybrid infrastructure and delivering it as high-fidelity, enriched telemetry to your SIEM (like Splunk or Microsoft Sentinel) for advanced analysis.
1. Feeding the “Single Source of Truth”
NFO ingests flow data from your switches, routers, and cloud gateways and streams it to your analytics platform in real-time. By providing a normalized view of every internal and external connection, NFO allows your SIEM to identify traffic directed at uncommon ports or subdomains that have never been registered with your API management layer.
2. Enabling Behavioral Analysis
Your SIEM’s ability to detect Shadow API patterns—such as “Low and Slow” scraping or credential stuffing—is only as good as the data it receives. NFO provides the granular, un-sampled flow data required for these platforms to spot subtle traffic surges coming from unauthorized endpoints.
3. Correlating Identity with Unknown Access
When your SIEM flags an unknown API, the first question is always: Who is using it? NFO answers this by enriching flow records with User and Device Identity before they hit your analytics engine. This allows analysts to instantly see if a specific service account is making requests to a legacy /v1/internal-transfer endpoint, providing the evidence needed to shut it down.
Conclusion: Bringing Shadow APIs into the Light
The modern network is under constant, sophisticated pressure. You can no longer afford to have blind spots in your API ecosystem.
By using NetFlow Optimizer to feed high-fidelity, identity-enriched telemetry into your security analytics platform, you can move from a reactive security posture to a proactive one—discovering and securing your Shadow APIs before an attacker exploits them.
Are you sure you know every API running on your network?
Contact us today to learn how NFO provides the telemetry you need for Shadow API discovery, or Schedule a Demo to see our integrations in action.
