The modern enterprise extends far beyond the data center and the laptop. It now includes countless devices on the network edge: everything from smart surveillance cameras and HVAC sensors to specialized Operational Technology (OT) controllers in a factory or warehouse. This growing ecosystem of Internet of Things (IoT) and Industrial Control Systems (ICS) dramatically expands your business capabilities, but also creates a massive security gap.
The sheer volume and nature of these edge devices present an insurmountable visibility problem for traditional security tools. You can’t secure what you can’t see, and you certainly can’t patch what you can’t touch.
The Limitations of Traditional Edge Security
Traditional endpoint security relies on two things: agents and constant patching. Neither is feasible for the vast majority of IoT and OT devices:
- Headless & Specialized Devices: Many IoT/OT devices are “headless” (lacking a user interface) or run highly specialized, proprietary operating systems. They cannot support security agents like EDR or anti-virus software. They are designed to do one job reliably, not to host complex security stacks.
- Operational Constraints: In industrial or healthcare environments, OT devices (like programmable logic controllers or life-support monitors) often cannot be patched or rebooted without scheduling disruptive downtime. Their operational integrity is prioritized over security updates, leaving known vulnerabilities exposed for years.
- Lack of Context: Even when logs are available, they often use proprietary or esoteric formats that traditional Security Information and Event Management (SIEM) systems struggle to interpret, making correlation virtually impossible.
Because of these constraints, the only way to effectively secure the edge is through agentless, network-centric monitoring.
Optimized NetFlow: Agentless Visibility at the Edge
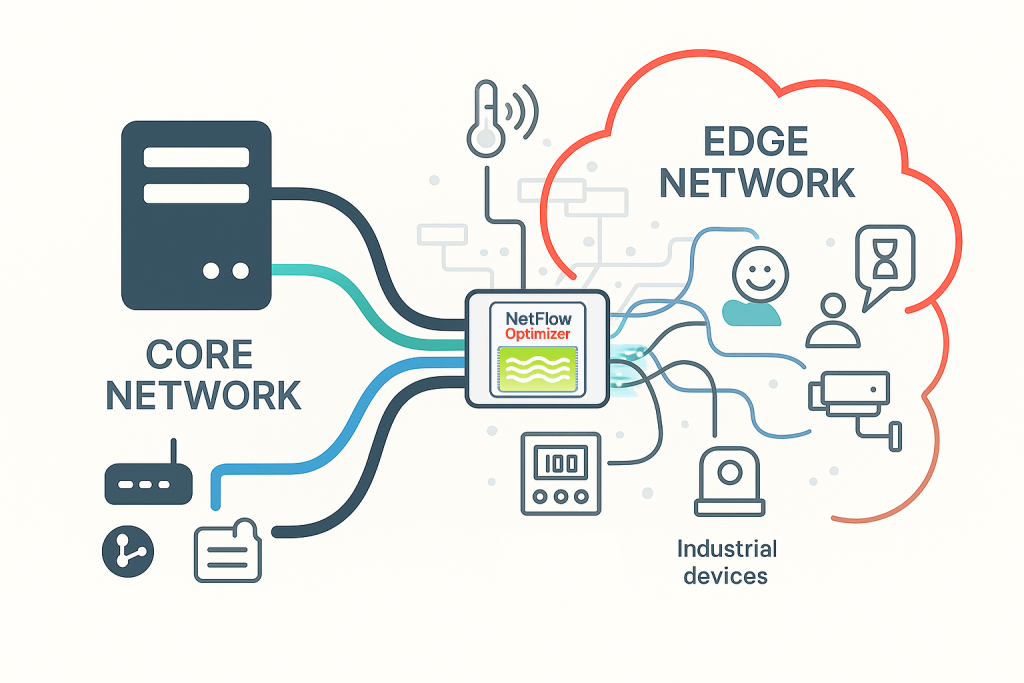
NetFlow, which records every connection, is uniquely suited to monitor these vulnerable devices because it’s passive, low-impact, and agentless. It doesn’t reside on the device itself; it is collected by the network gear already routing the traffic.
NFO’s Role: Preparing High-Fidelity Data for Edge Security
Securing the network edge, particularly with numerous headless IoT and specialized OT devices, requires agentless visibility. NetFlow Optimizer (NFO) fulfills this requirement by acting as the critical data pre-processor, preparing raw flow data into the rich, AI-ready intelligence required by your SIEM, SOAR, and IT Operations systems for autonomous analysis and action.
1. Building the Clean, Contextual Baseline
IoT and OT devices exhibit highly predictable communication patterns (e.g., a temperature sensor only talks to its central gateway every 60 seconds). NFO’s role is to ensure that the systems tasked with establishing this baseline receive high-quality data:
- Volume Reduction: NFO performs intelligent deduplication and aggregation of redundant flows. This reduction ensures that the analytics engines building the behavioral baseline are not bloated with irrelevant data, allowing for faster processing and more accurate baseline modeling.
- Contextual Enrichment: NFO adds the crucial context that transforms a generic flow into an identifiable asset. It enriches the flows with vital identity and asset information (e.g., “Finance-VM-SQL01” instead of an IP, or “User JaneDoe” instead of “192.168.1.50”), tying the traffic directly to the physical or virtual asset and making its baseline behavior instantly recognizable and actionable for downstream systems.
2. Fueling Anomaly and Policy Violation Detection
NFO ensures that the downstream SIEMs and analytics platforms have the rich, contextual data needed to identify subtle shifts that signal a compromise or policy violation—something raw NetFlow alone cannot support.
- High-Fidelity Input: The enriched data stream enables the analytics platforms to easily spot shifts like an Unusual Communication (e.g., detecting when a sensor talks to an unexpected external IP address) or Protocol Abuse (e.g., a device running its normal protocol but communicating with an unexpectedly high frequency).
- Enabling Forensic Analysis: NFO provides the necessary context for Post-Compromise Activity analysis, ensuring that when an attacker uses a compromised edge device, the resulting traffic flows are immediately tied to the asset and its communication history, allowing the SIEM to flag the activity.
3. Enabling Agentless Network Response
Since the security team cannot install a response agent on specialized edge devices, the response must happen on the network layer. NFO’s contribution is providing the high-quality input required to trigger this rapid automation:
- Actionable Intelligence Delivery: NFO feeds the high-fidelity, contextual data—complete with the infected device’s identity and precise communication details—directly into a Security Orchestration, Automation, and Response (SOAR) platform.
- Automated Action Trigger: This rich input enables the SOAR platform to instantly trigger an automated playbook to execute network-layer defensive actions, such as:
- Isolate the Device: Immediately quarantine the traffic from the compromised OT controller at the nearest switch or firewall.
- Block Malicious Flow: Update access control lists to block the specific anomalous flow, stopping the attack without disrupting the rest of the network.
Conclusion: Securing Tomorrow’s Network Today
The network edge is the future battleground for cybersecurity. You cannot secure the increasing presence of IoT and OT devices using yesterday’s security tools. Optimized NetFlow provides the only viable, low-impact, and agentless path to achieving the visibility required to monitor and protect these specialized environments.
By transforming raw network telemetry into precise, contextual intelligence, NetFlow Optimizer ensures your security team can proactively monitor and manage the vast, expanding attack surface of the network edge.
Contact us today to learn how NetFlow Optimizer can provide the agentless visibility needed to secure your critical IoT and Industrial Control networks.
You can also schedule a demo to see how our NetFlow Optimizer handles your specialized edge traffic.
