In the relentless battle against cyber threats, organizations are increasingly turning to Artificial Intelligence (AI) to gain an edge. Yet, many struggle to truly harness AI’s power, particularly when it comes to network security. The culprit? Often, it’s the sheer volume and raw nature of the data itself.
One of the richest sources of network insights is NetFlow (along with IPFIX and sFlow). It captures every conversation on your network, detailing who’s talking to whom, for how long, and over which protocols. In theory, this data is gold for security. In practice, however, raw NetFlow is extremely voluminous, a data tsunami that can overwhelm even the most robust SIEM (Security Information and Event Management) and IT Operations systems. You simply can’t feed raw, unchecked NetFlow directly into your AI models and expect meaningful results.
The Problem with “Naked” Data: Why Volume Reduction and Enrichment Are Non-Negotiable
Imagine trying to build a complex structure with raw, unhewn timber that weighs a ton. That’s what feeding unoptimized NetFlow into your security stack feels like. The first critical step is volume reduction. Without it, you’re not just wasting storage and processing power; you’re creating bottlenecks that prevent timely analysis. Our NetFlow Optimizer tackles this head-on, intelligently reducing data volume by combining similar flow records. This means you send only high-fidelity data, with similar flow records intelligently combined to ensure no information is lost, to your SIEM, saving on ingestion costs and improving performance.
But reducing volume is only half the battle. Raw NetFlow provides “naked IP addresses.” Try feeding those into an AI algorithm, and you’ll quickly realize how useless they are on their own. For AI and Machine Learning (ML) to truly shine, data needs context. This is where enrichment comes in.
Our NetFlow Optimizer transforms this raw data into quality data, suitable for ML and other AI applications, by adding vital context:
- User Information: Linking IP addresses to specific users for identity-based correlation.
- Asset Information: Associating IP addresses with specific servers, applications, and devices.
- Threat Intelligence: Flagging flows communicating with known malicious IPs or domains. (Learn more about integrating threat intelligence here).
- Geolocation Data: Providing geographical context for network connections.
This enrichment provides the essential labels and relationships that allow AI algorithms to identify anomalies, recognize patterns, and detect threats that “naked” IP addresses simply can’t reveal. It’s the difference between seeing a car on the road and knowing who’s driving it, where they’re going, and if they’re on a suspicious watch list.

Leveraging Your Investments: The Power of Integration
Most organizations have already made substantial investments in their SIEM and IT Operations systems. These platforms are the central nervous systems of your security and operational intelligence. The good news? You don’t need to replace them to achieve AI-powered network security. Instead, you need to empower them with better data.
This is where the seamless integration of optimized NetFlow data becomes a game-changer. By feeding your existing SIEM and IT Ops systems with reduced and enriched NetFlow, you leverage your organization’s investment in these critical platforms. This integration enables powerful correlation of NetFlow with other machine data already collected in these systems—logs, endpoint telemetry, vulnerability scans, and more. Suddenly, your SIEM can connect a suspicious network flow to a specific user login, an alert from an endpoint, or an unusual access pattern, providing a truly unified and holistic view of your security posture.
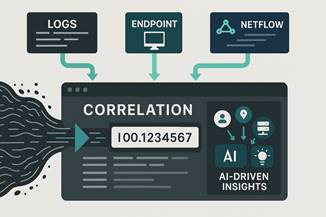
Your Foundation for AI: The NetFlow Optimizer
Implementing AI in network security isn’t just about deploying a fancy algorithm; it’s about building a robust data foundation. Our NetFlow Optimizer is that foundational tool. It’s the critical first step for any organization serious about implementing AI in their network security strategy. Learn more about NetFlow Optimizer and its recognition by industry analysts like Gartner here.
It tackles the twin challenges of overwhelming volume and contextual emptiness, transforming raw NetFlow into the high-quality, actionable data your AI needs to thrive. Without this crucial optimization, your AI initiatives risk drowning in irrelevant data, providing only partial insights, or worse—generating false positives that fatigue your team.
Ready to Transform Your Security Operations?
Empower your security and IT Ops teams with the deep network visibility they need. Discover how our NetFlow Optimizer prepares your data—reducing volume while enriching every flow record—to fuel your existing SIEM and IT Ops investments.
Visit our website today to explore our solution and request a personalized demo.
