The firewall stands as the first line of defense, a stalwart guardian protecting your network’s perimeter from external threats. It meticulously examines north-south traffic, diligently blocking malicious intrusions and unauthorized access attempts from the outside world. But what happens once a threat breaches those outer walls? What about the dangers lurking within, moving laterally or acting from the inside? This is where traditional perimeter security often falls blind, and where the power of enriched NetFlow shines.
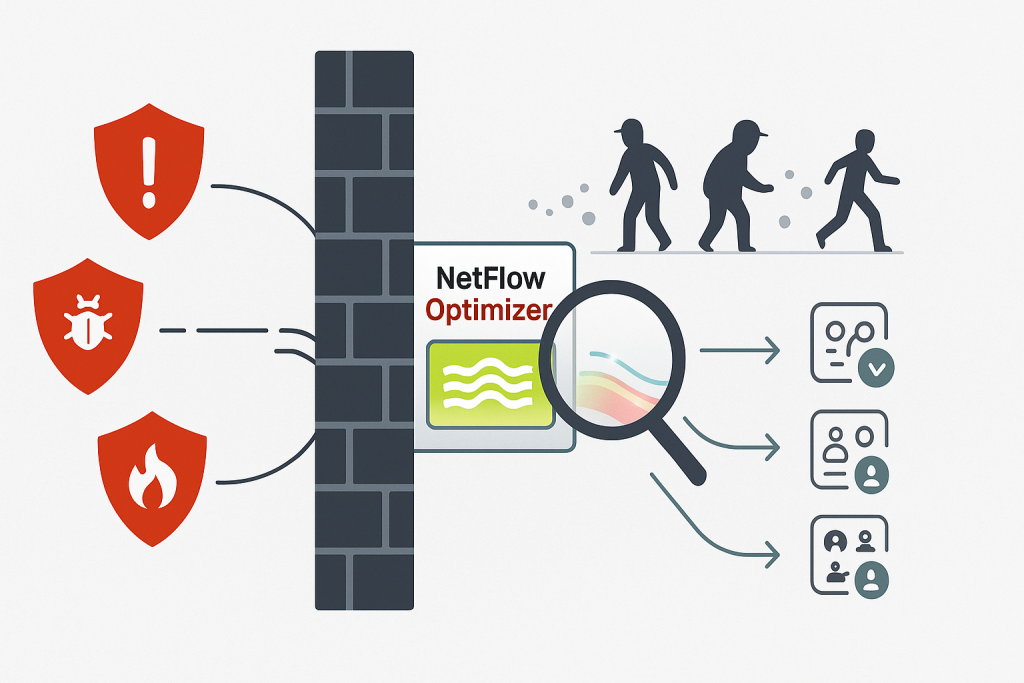
In our ongoing exploration of leveraging NetFlow data for enhanced network visibility, we’ve highlighted its capabilities in areas like performance monitoring and threat hunting at the perimeter. Today, we delve into a critical security blind spot: the activities happening inside your network.
Firewalls, while essential, primarily focus on controlling traffic entering and leaving your environment. They have limited visibility into the east-west traffic – the communication between devices and users within your internal network. This is precisely the space where attackers, having bypassed initial defenses through techniques like phishing or exploiting vulnerabilities, often operate undetected. They move laterally, hopping from one compromised system to another, seeking valuable data or establishing a stronger foothold. Similarly, insider threats, whether malicious or unintentional, operate entirely within this internal landscape.
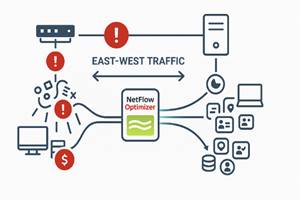
This lack of internal visibility is a significant challenge for security teams. How can you identify a compromised endpoint attempting to access sensitive databases on another server? How can you detect an employee exfiltrating data to an unauthorized external location from their workstation? The answer lies in the detailed insights provided by enriched NetFlow data.
Unlike basic NetFlow, which primarily captures source and destination IP addresses and ports, enriched NetFlow data incorporates crucial contextual information. By integrating with identity management systems, directory services, and endpoint security tools, our NetFlow Logic solution can associate network flows with:
- User Identity: Knowing who is generating the traffic, not just the IP address.
- Device Details: Understanding the specific endpoint involved, its vendor, type, and its role within the network.
- Application Context: Identifying the specific applications and processes generating network communication.
This rich contextual data transforms simple flow records into powerful security intelligence. Suddenly, those “naked IP addresses” gain identity and purpose, allowing you to see the complete picture of network activity, including lateral movement that would otherwise remain invisible to perimeter-focused tools.
Here are concrete examples of how enriched NetFlow helps detect internal threats:
- Lateral Movement Detection: An unusual pattern of communication from a standard user workstation to multiple servers it doesn’t typically access can be a strong indicator of a compromised account or endpoint attempting to spread within the network. Enriched NetFlow reveals the user associated with that workstation, the specific servers being contacted, and the applications being used for these lateral connections.
- Rogue Device Identification: The sudden appearance of network traffic originating from an unknown or unauthorized MAC address can signal the presence of a rogue device. Enriched NetFlow can help pinpoint the device’s activity and its communication patterns, aiding in rapid containment.
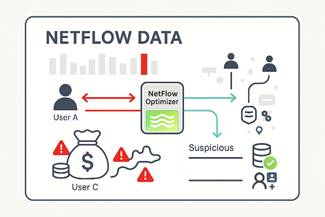
- Unauthorized Data Access: Attempts by a user or device to access sensitive data repositories or file shares outside their normal access permissions can be flagged based on the enriched context associated with the network flow.
- Compromised Credentials: After initial infiltration, attackers often use compromised credentials to move laterally. Enriched NetFlow can help identify suspicious activity associated with a specific user account, such as logins from unusual locations or access to resources beyond their typical scope.
- Insider Threat Detection: Unusual data exfiltration patterns, such as large file transfers to external IP addresses or unauthorized cloud storage services initiated by an internal user, can be readily identified through enriched NetFlow analysis.
In today’s threat landscape, adopting an “assume breach” mentality is crucial. It’s no longer a question of if an attacker will get in, but when. Therefore, robust internal visibility is paramount. Our NetFlow Optimizer plays a vital role in this strategy by not only reducing the volume of NetFlow data but also ensuring it’s enriched with the critical context needed to detect these subtle, internal threats. By providing high-quality, actionable data, the NetFlow Optimizer empowers your security teams to see beyond the firewall and identify malicious activity that might otherwise go unnoticed.
Don’t rely solely on perimeter defenses. Gain the deep internal visibility you need to detect lateral movement and insider threats with enriched NetFlow. Request a personalized demo of our NetFlow Logic solution today and take a crucial step towards a more resilient and secure network.
